Military Cac For Mac No Client Certificate Presented
Applicable Products
- Access Gateway 10
Is your CAC reader Mac friendly? Mac os x 10.5 leopard dmg. Visit the USB Readers page to verify the CAC reader you have is. I will teach you how to gain CAC access to military websites if you are a DOD employee. This works for all branches of service. .CAC Reader Driver (reader “talks” to computer).ActivClient (card “talks” to Windows).LotusForms (view forms) (replaced PureEdge).ApproveIt (sign forms).All software is accessed using your AKO username / password. However, do download Lotus & ApproveIt requires you can login with your CAC first.
Objective
This article describes how to Integrate Web Interface 5.3 and Access Gateway Enterprise for Pass-through Access.
Requirements
XenApp and Web Interface servers must be domain members
XenApp XML service must be running with IIS on the XenApp farm. This is because Kerberos authentication is done by IIS on the Smart Card user’s behalf
Smart Card middleware is no longer needed to be installed on Web Interface or XenApp servers. This is because this process uses Kerberos for authentication
Access Gateway Enterprise 9.2 Build 48.6 or later must be used
Web Interface 5.4 build 51 must be used
Web Interface must not be installed on a Domain Controller
XenApp 4.5 and 5.0 have been tested
XenApp 6.0 requires fix #242752 which is currently available in XA600W2K8R2X64R02, CTX133882 ‑Hotfix Rollup Pack 2 for Citrix XenApp 6 for Microsoft Windows Server 2008 R2 (Included in XenApp 6.5)
Active Directory domain functional level must be 2003, 2008 or 2008 R2
Instructions
Complete the following procedures accordingly:
Active Directory Configuration
Complete the following steps to configure Active Directory:Configure Delegation for XenApp and Web Interface servers.
Web Interface must delegate http service to all XML servers.- The XenApp server must delegate http and host service to themselves plus host and http service to all XenApp servers. Each XenApp server must also delegate CIFS and LDAP services to the Domain Controllers. Note: The examples of Constrained Delegation, as demonstrated above, are meant to be examples of the minimum configuration required to allow logging on. If a Published Desktop or Published Application uses other resources not on the XenApp server itself (for example, CIFS file shares, SQL, DCOM) additional configuration might be required. Any server hosting that resource must be configured to allow for the XenApp server to access the resource. The correct Service Principal Names (SPN) must be configured for those resources.
Web Interface Configuration
Complete the following steps to configure web interface:- Create a Web Interface site with authentication set to at access gateway.
- The proper Gateway URL must be entered and resolvable from the Web Interface server in addition to Smart Card being selected.
- Enable smart card pass-through.
Reboot the Web Interface.
XenApp Configuration
Complete the following steps to configure XenApp:- Set each XenApp server to trust XML requests.
Note: On XenApp 6.x, this location has changed to the server policy being used.
- Then, when configuring the Web Interface site, ensure that the XenApp servers are defined with their fully qualified domain name, which itself must be resolvable by Web Interface. The fully qualified domain name MUST match its name in Active Directory. Failing to do this causes Kerberos authentication to fail and an Access Denied error page to appear.
Access Gateway Configuration
Complete the following to configure Access Gateway:
Military Cac Certificates
The Access Gateway virtual server must have all necessary CA certificates bound as CA certificates. In case the certificate for the Smart Card has an intermediate authority, both the intermediate and root must be bound separately as CA certificates.
Configure the Access Gateway virtual server with client certificate optional.
Otherwise, the callback from Web Interface FAILS.- Configure an authentication policy forcing a client certificate to be presented. If this is not configured, anyone will be able to log on.
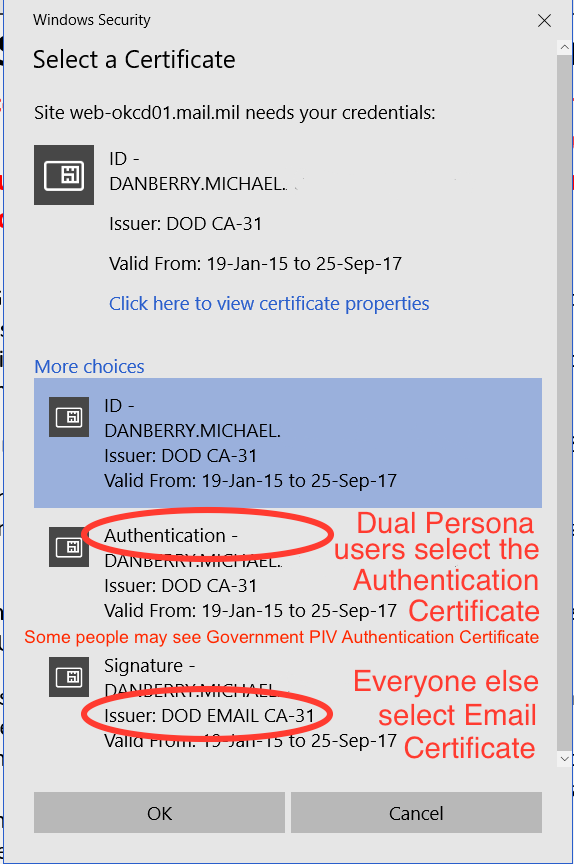
- Depending on Active Directory configuration the profile might need to use the Alternate Subject Name on the Smart Card. This would be the case with DoD CAC Smart cards and also cases where there are multiple CN attributes identifying the user. Important! If not using SubjectAltName for the user name field, a Single Sign-On Domain must be configured either on global settings or the session profile.
The profile does not necessarily have to be configured with group information. However, if configured, Access Gateway performs group extraction based on the criteria chosen for it. The most important configuration on Access Gateway Enterprise is the Single Sign-on (SSO) Domain field within the session profile and global setting. A new knob has been introduced on Access Gateway Enterprise where, if a SSO name is entered, the UPN from the Smart Card certificate is split in half. This is very important to understand, and in case of DoD CAC cards, this field must be left blank from both global settings and the session profile. When the field is left blank, Access Gateway forwards the user name in full UPN.
To control this behavior, there is a new shell command (Note: This is shell command and not CLI command). The name of the variable is wi_sso_split_upn. If non-zero and Single Sign-On domain is not set, UPN splits into username and domain during SSO to Web Interface. If zero, UPN is used for SSO to Web Interface.
To change the variable value, if necessary, connect using SSH, type shell, and then type nsapimgr –ys wi_sso_split_upn=1. Note: There should be very few situations where it is necessary to change this value from the default value.
In summary, there are four possible scenarios:
- If SSO domain is entered and this variable is default, UPN is split in half.
- If SSO domain is entered and this variable is changed to anything other than 0, UPN is split in half.
- If SSO domain is not entered and this variable is default, UPN is used for SSO with Web Interface.
- If SSO domain is not entered and this variable is changed to anything other than 0, UPN is split in half.The URL for Web Interface in the Session Profile (or Global Settings) must use SSL. This means that a SSL certificate must be properly installed on the Web Interface server.
Issues Seen During Implementation
During implementation of this configuration on a pure Windows 2008 Environment and Citrix XenApp 5.0 a XenApp hotfix had to be installed. The hotfix addressed an issue where upon launching a published application the connection would be terminated and the DNS Client Service on the XenApp server would terminate. The hotfix that addressed this issue is CTX125414 ‑ Hotfix Rollup Pack 1 for Citrix XenApp 5.0 for Microsoft Windows Server 2008 32-bit Edition, XAE500W2K8R01.- While attempting to launch a published application Web Interface would report “The resource is no longer available” on the web page. This would prevent an ICA file to be created and the server would log on Event Viewer:
Site path: C:inetpubwwwrootInternalSmartCard.The XML document sent by the Citrix servers could not be processed because it contains invalid XML. This message was reported from the XML Service at address http://xa50.repro2k8.net:80/scripts/wpnbr.dll [com.citrix.xml.NFuseProtocol.RequestLaunchRef]. The specified Citrix XML Service could not be contacted and has been temporarily removed from the list of active services. [Unique Log ID: da4f1ad1]
To correct this issue the Local Computer policy was adjusted to allow logon locally for Domain Users. Smart Card implementation for Gemalto Gemplus Smart Cards requires Gemalto “Classic Client” for Firefox integration on a Red Hat system. This software must be purchased from Gemalto and is not freely available
- DoD CAC Smart Cards in a Linux based operating system can be used with the use of a freely available library called “coolkey”. On an Ubuntu operating system the packages added were: libusb-0.1-4, libpcsclite1, libpcsclite-dev, pcscd, and pcsc-tools (the actual command was “sudo apt-get install libusb-0.1-4 libpcsclite1 libpcsclite-dev pcscd pcsc-tools build-essential autoconf xlibs-dev libccid”)
Firefox was then configured to load libcoolkeypk11.so under Tools > Options > Advanced > Encryption > Security Devices. On a Windows machine if Firefox is intended to be used, additional configuration is needed. Under Tools > Options > Advanced > Encryption > Security Devices a new Device must be loaded. The DLL to be loaded for a GemPlus Smart Card is called gclib.dll and it is usually placed under Program FilesGemplusgemSafe Libraries UserBIN
- While launching a published application the user would start the session, login to the server, but the server would quickly report “Access is denied” before displaying the application. The same user would be able to login through RDP or using an Explicit login to Web Interface. This issue is currently under investigation but to get around the problem the registry DWORD IgnoreRegUserConfigErrors was created under HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server.
Military Cac For Mac No Client Certificate Presented Completion
Known Limitations
This configuration causes two PIN prompts from the user if connecting from a non-domain member or if the client machine is a domain member but using Windows Vista or later.This first condition occurred because the user logged on to Windows and did not log on with the Smart Card. Therefore, the ICA client cannot grab and provide smart card information from Winlogon.
The second condition occurred because of a change in security done by Microsoft on Windows Vista and later. On Windows Vista/7 the behavior of Windows has changed. Upon a smart card logon the mpnotify.exe process is simply not invoked by Winlogon.exe anymore (it is still invoked for username/password logon). The only way we currently know to capture the smart card logon PIN on Vista/7 is to install a credential wrapper. However, this is not something recommended by Microsoft.Additional Resources
CTX131223 - Enabling Smart Card PIN Pass-Through on Windows Vista or Windows 7 Citrix Session
If this workaround is not applied, a PIN prompt is displayed by the browser.
And a PIN prompt from the XenApp plug-in when launching an application.
Many enterprise IT systems at NPS make use of SSL certificates issued by the DoD. If your browser doesn't trust them, you may run into issues. Reinstalling the certs is always a good step in troubleshooting as well. Get started with installing the latest certificates by reviewing the tutorials below.
InstallRoot Tool
The InstallRoot application is the simplest and most straightforward way to install all DOD certificates in your windows operating system, and supports Internet Explorer, Chrome, Firefox, and Java.
- Select your corresponding computer architecture type from the links below: (NIPR Windows Installer, for SIPR certificates access DISA's site directly from a SIPR machine)
- Once downloaded, install the file and run InstallRoot.
- Install required certificates. A more detailed explanation with pictures is shown below.
- Restart your browsers for the changes to take effect (all windows!).
- In some cases you may have to clear the cache of the browser you are using.
Download the Install Root Software here:
Step 1:
Double-click the installer and click next.
Step 2:
Select the desired folder to install to or continue by clicking next.
Step 3:
Leave the defaults checked and click next.
Step 4:
After the installation finished click run InstallRoot.
Step 5*:
If Firefox, Java, or both programs are installed on your computer you will be asked if you would like to install the certificates in their respective certificate stores. Select yes if you are accessing DOD sites that use Java or if you access DOD sites with Firefox.
Step 6:
Close the Quick Start pop up.
Step 7:
Click Install Certificates in the top left corner. If you click the drop down next to the red ribbon you should see a green check mark next to the certificates.
Military Cac Certificates Mac
More information on certificates and other tools can be found via DISA.
Military Cac For Mac No Client Certificate Presented Deposit
Download the latest DoD root certificates here:DoD RootCerts file (CAC required).
No Client Certificate Presented Cac Card
- Open the Keychain Access application if it's not already running.
- Drag certificates in the folder to the login section of the Keychain Access.
- Click 'Add' to pop-up adding all certificates to login keychain (must click add to every certificate.).
- Once all certificates have been added double click DoD Root CA 3 and 4 certificates, select Trust and change 'When using this certificate' from 'User System Defaults' to 'Always Trust'.
- Confirm your changes by entering an administrative password.
Cac Card No Client Certificate Present
Notes:
There should be 55 DoD certs available in the Mac Keychain Access Utility.